How to automate security with AWS?
Security is a growing concern across organizations. Almost 65% of successful intrusions remain undetected despite having security solutions in place.1 Besides, 95% of cybersecurity threats are caused by human error in some or the other way says the Global Risks Report released by the World Economic Forum.2
Well, there’s a way to kill these two birds with a single stone. – Automate security with AWS!
AWS not only empowers you with control and gives you the confidence to securely run your business but also allows you to automate manual security tasks without any human intervention. This way you can focus on scaling and innovating your business while AWS keeps the cloud computing environment secure from breaches.
Quick Case Study: iLink helped a client securely migrate core services to the cloud.
Though there’s a lot to the story, we would like you to know the basics first. In the blog post, you’ll learn about security automation, why organizations are adopting it and how you can implement it within your AWS environment. This article aims to introduce you to the core concepts of security automation and implementation considerations to help you get started.
What is Security Automation?
As the name suggests, security automation is a technology-based execution of security actions with reduced human assistance. It is the process of integrating security in applications and infrastructure to programmatically detect, investigate and remediate cyber threats. Automating security does most of the work for your security team. They no longer have to manually identify every incoming threat, address them and prioritize alerts as they come.
Other than this, security automation has the potential to triage threats by following instructions from security analysts, determining if the issue is legitimate and whether to take action in response. The cherry on the cake is – all of this can happen in mere seconds without any human help.
Why automate security with AWS?
As workloads grow in size and complexity it becomes increasingly difficult to manually manage security and compliance within your AWS environment. Moreover operating them manually results in slower identification and remediation of issues, also leading to missing errors in resource configuration making your systems vulnerable to compliance issues.
Automating security with AWS helps to quickly detect and respond to security alerts. Your organization can avoid unplanned and expensive downtime. It also helps you scale security operations as you expand your workloads running on AWS increasing functionality for your environment.
You can streamline your daily operations, and integrate security into IT infrastructure, applications, hybrid cloud structure, and processes right from the start. Fully deploying security automation can even reduce the average cost of a breach by 95%.3
How to implement Security Automation with AWS tools?
- Classify workloads and define controls
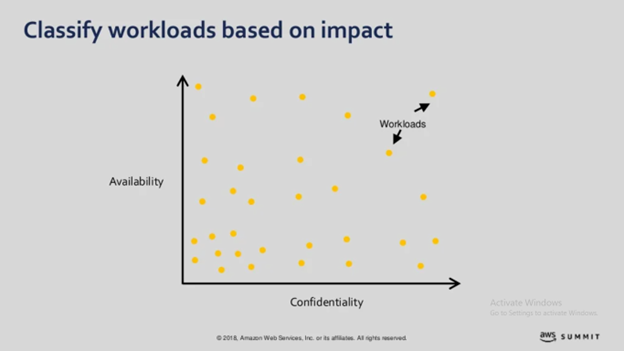
To classify your workload, it’s important to first understand its impact. Think of two axes graph – Availability vs. Confidentiality. Now your workloads could be individual applications or individual developer environments, classified as the following on the graph.
Type of workload | Availability | Confidentiality |
Individual Applications | Low | Low |
Team development test environment / Low-risk apps | Medium | Low |
Web Digital | High | Low |
Analytics on sensitive data | Low | High |
Sensitive internal applications | Medium | High |
Critical Applications | High | High |
The key concept here is that the controls are additive. If you have a set of security controls to build on, you can define how you want to implement those in terms of coding configuration. In a low-risk environment, you have a handful of essential controls that can build up into your medium-risk environments and further on into high and high environments.
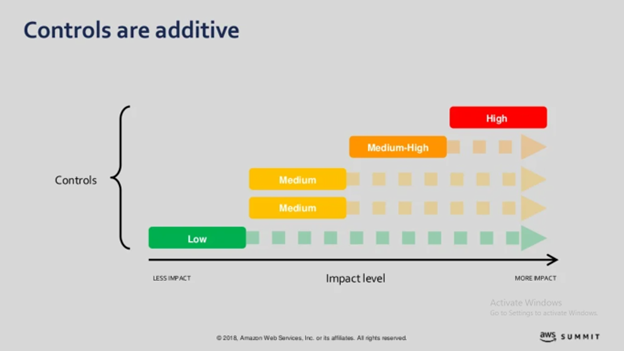
The work you do with lower levels helps you build your repertoire of controls or repertoire tools as you start moving more and more sensitive and critical data into your cloud.
2. Provision and baseline your environments
AWS organizations have newer functionality that allows you to have policy-based management for multiple AWS accounts. You can also create a single master account, and create newer AWS child accounts under the same using organization’s API or the console. You can organize these accounts into groups and then apply policies to those groups. This way you can restrict services available within individual subunits, consolidate bills for your accounts and use a single payment method.
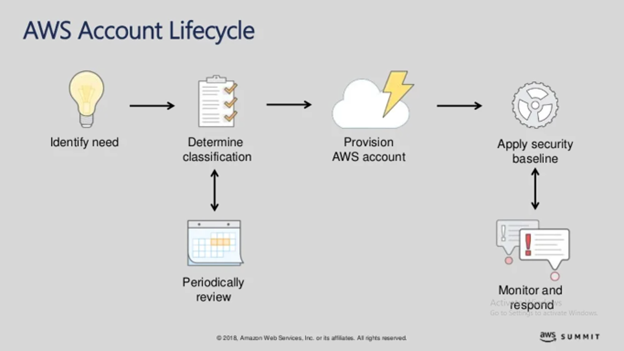
Looking into the AWS account lifecycle, first, you have to identify the need to create the account. Maybe for the developer who needs a test environment or a team that wants to host their continuous integration pipeline or a product account for a new service. Then identify and classify the security risk inheriting this account and then provision automatically using the organization’s API.
Apply security baseline to that following the classification you have determined. As part of the process, monitor response to incidents in that account by using an implementation of control defined and then periodically review and rebase the line. It will help you maintain data and a spreadsheet about who owns which accounts and keep them in compliance.
3. Secure and monitor AWS config
Securing and monitoring AWS configuration make it simple to assess, audit, and record configurations and changes by defining the desired configuration state of your AWS resources. It provides several AWS-managed rules that address a wide range of security concerns.
Some of them include checking the encryption of your Amazon Elastic Block Store (Amazon EBS) volumes, tagging your resources appropriately, and enabling multi-factor authentication (MFA) for root accounts. It also helps to create custom rules to codify your compliance requirements.
4. Secure and monitor your workloads
Some of the best practices to secure and monitor your workloads are – leveraging multi-factor authentication, using identity and access management, implementing end-to-end encryption, maintaining strong visibility in the cloud environment, and educating employees. This will enable you to harden your security posture and provide protection as you continue to scale.
5. Respond and Remediate
You can automate your AWS services to respond automatically to system events such as application availability issues or resource changes. Events from AWS services are delivered in near-real-time and on a guaranteed basis. You can write simple rules to indicate which events you are interested in and what automated actions to take when an event matches a rule.
Feel birds spinning around your head? iLink can help.
As an AWS Consulting Partner, iLink offers specialized services to help customers of all sizes design, build, migrate and manage their workflows on AWS to accelerate their Cloud journey. We understand our customer’s needs, help them identify solutions that meet their business requirement, and more importantly, expose the areas of risk to mitigate and eliminate them.
Endnotes
- https://governmenttechnologyinsider.com/cyber-threats-65-percent-go-undetected-by-todays-organizations/#:~:text=Cyber%20Threats%3A%2065%20Percent%20Go%20Undetected%20by%20Today’s%20Organizations,-by%20Jackie%20Davis&text=When%20discussing%20cyber%20security%2C%20government,that%20affect%20their%20cyber%20systems.
- https://www3.weforum.org/docs/WEF_The_Global_Risks_Report_2022.pdf
- https://www.redhat.com/en/engage/idc-ansible-automation-s-201906060343


