Modernizing Your Security Operation Center (SOC) with Microsoft Sentinel SIEM

Introduction
According to a Forrester study, “Organizations deploying Microsoft Sentinel are realizing a remarkable 234% ROI, over the period of three years”.
As businesses are increasingly adopting cloud databases, hybrid infrastructures, and the rapid proliferation of IoT devices, the attack surface continues to expand at an unprecedented pace. Moreover, the sheer volume of security alerts across endpoints, cloud platforms, servers, and databases are often hindering security analysts to hold their line of defense. Traditional SoC often falls short in addressing the scale and sophistication of today’s cyber threats. With thousands of security alerts shifting through daily, SoC analysts are demanding SoC modernization to streamline and automate security workflows while ensuring robust security and operational integrity.
Microsoft Sentinel is a trusted and AI-powered threat intelligence platform that modernize our legacy on-premises SIEMs to proactively detects, respond, and mitigate threats faster and more efficiently.
This blog aims to delve into how Microsoft Sentinel modernize our existing SoC and empower SoC analysts to proactively manage threats and prevent the SoC analysts’ burnout.
Challenges in Traditional SoC
Traditional SIEM platforms have served as the backbone of security operations, are now struggling to keep pace with modern cybersecurity demands.
Here the major challenges faced in the legacy on-premises SIEMs
- High Costs: The upfront investment, extensive configuration expertise, ongoing maintenance, and skilled personnel required to operate traditional SIEM systems are substantial.
- Complex Pricing Models: Many traditional SIEM solutions have opaque pricing structures, often based on data volume, which can restrict comprehensive data collection and analysis.
- High False Positives: Legacy systems frequently generate excessive false positives, overwhelming analysts with non-actionable alerts and reducing the effectiveness of threat detection.
- Limited Support for Hybrid Infrastructures: As organizations shift to hybrid and multi-cloud environments, traditional SIEMs often lack the flexibility and integrations needed for seamless operations.
These limitations highlight the need for a more robust, agile, and intelligent approach to threat detection and response.
Modernizing SOC with Microsoft Sentinel SIEM
Microsoft Azure Sentinel is a next-generation SIEM and SOAR platform that transforms SoCs by integrating advanced threat detection, automation, and integration capabilities. This cloud-native platform is powered by built-in AI, threat intelligence, security log analytics, custom alert rules, and automated playbooks that helps to meet the demands of modern security operations by collecting, detecting, investigating, and responding to security alerts in real time.
The massive data analytics capabilities of SIEM help enterprises analyze a large volume of data stemming from applications, users, devices, and servers. Microsoft sentinel serves as a unified platform providing a view of bird’s-eye view of enterprise security incidents, unique insights and threat intelligence feeds that go beyond internal logs through leveraging machine learning models.
iLink’s Four-Step Framework for Microsoft Sentinel in SOC Modernization
Azure Sentinel leverages a four-step framework to modernize SOCs:
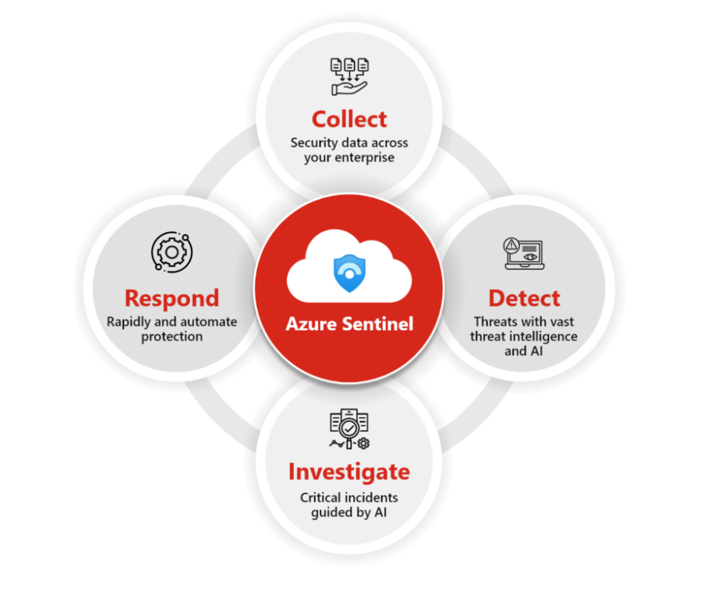
- Collect: Aggregates data across users, devices, applications, and cloud environments, ensuring comprehensive visibility.
- Detect: Uses AI and machine learning to identify anomalies and detect threats in real-time.
- Investigate: Provides interactive investigation tools, allowing analysts to delve into incidents with granular detail.
- Respond: Automates incident response using playbooks, reducing the time and effort required to neutralize threats.
Core Components of Microsoft Sentinel SIEM
Data Collection: Azure sentinel collects data seamlessly from diverse resources, ranging from users, applications, infrastructure, and networks across on-premises and multi-cloud environments that are connected to Azure as it can seamlessly integrate with other Microsoft advanced security solutions, including Windows Defender, Cloud App Security, and Azure Security Center.
Universal Visibility & Analytics: By integrating SIEM and the incident response platform, Next-gen SoC offers a unified view into the cybersecurity posture by providing a centralized interface that correlates security incidents for collaborating stakeholders’ responses to make more informed security decisions.
Advanced Threat Investigation and Threat Hunting: Next-Gen SOC offers interactive and deep threat investigation capabilities across the organization’s IT networks and multi-cloud environments. Furthermore, it detects external sources such as the dark web and social media for any potential threats. Azure Sentinel can create custom alert detection rules and detect risk alerts and previously uncovered threats by leveraging AI and machine learning, proactively detecting threats across organizations, and ensuring streamlined incident identification. Using threat intelligence platforms and malware analysis technologies, we can gather data and malware samples from open-source intelligence and close feeds. This helps in giving insights into the tactics, techniques, and procedures (TTPs) used by cybercriminals.
Threat Remediation with SOAR Platform: SOAR capabilities of Azure sentinel automate rudimentary tasks, such as sending alerts to responsible SoC analysts to quarantine and block infected systems from the network by proactively monitoring the status of escalating incidents. As it can seamlessly integrate with other enterprise tools, such as Microsoft Teams, Jira, Zendesk, and Slack, it ensures seamless collaboration and communication among stakeholders through video conferencing and chats.
Choosing the Right Managed Microsoft Sentinel Services Provider
Selecting the right Azure Sentinel Managed Security Services Provider (MSSP) is a critical step in maximizing the potential of your security operations. A skilled MSSP can transform Microsoft Sentinel into a powerful asset for protecting your organization against evolving threats. Here’s a comprehensive guide to key factors you should consider:
- Security Expertise: Evaluate the MSSP’s proven experience with Microsoft Sentinel and advanced cybersecurity. A deeper understanding of the latest threats and certifications like SOC 2 or Microsoft Security Analyst.
- Advanced Capabilities: Employ layered defense strategy with AI-driven insights, including threat hunting and incident response, to enhance threat detection and reduce false positives.
- Seamless Integration: Expertise in integrating Sentinel with tools like XDR, MDR, and Threat Intelligence. Unified workflows connecting cloud, on-prem, and third-party solutions.
- Scalability: Flexibility to grow with your organization’s evolving security needs. Dynamic resource allocation for peak activity or expansions.
- Comprehensive Services: Ensure the MSSP offers a comprehensive suite of sentinel services, including 24/7 monitoring, threat hunting, incident response, compliance support, and automation. They should encompass proactive strategies to detect vulnerabilities and reduce MTTR.
- Cost-Effectiveness: Analyze and compare the various transparent pricing models offered by MSSP that align with your budget, ensuring good ROI through reduced breaches and operational efficiency.
Benefits of Next-Gen Microsoft Sentinel SIEM & SOAR Solutions
Integrating Microsoft Sentinel SIEM into your SOC delivers unparalleled benefits, including:
- Continuous Discovery of Vulnerabilities: Automatically identifies misconfigurations and potential weaknesses, enabling proactive remediation.
- Prioritized Remediation: Context-aware insights help prioritize threats based on business impact and relevance to the evolving threat landscape.
- Enhanced Detection and Response: Endpoint Detection and Response (EDR) alerts provide detailed breach insights, enabling swift action.
- Vulnerability Correlation: Connects endpoint vulnerabilities with broader threat patterns for holistic security insights.
- Integrated Remediation Processes: Offers seamless integration with tools like Microsoft Intune to automate remediation workflows, minimizing downtime and manual intervention.
Embrace the Future of SOC Modernization
As the cyber threat landscape continues to evolve, organizations began modernizing their SOC with Next-generation SIEM and SOAR. iLink has extensive experience in Azure sentinel services, including attach detection, threat visibility, proactive hunting, and threat response that prevent major cyber-attacks like Ransomware, Log4J, and other threats/exploitations.
As a trusted Microsoft Gold Level partner, our team of experts guides you through every stage of your modernization journey, from deployment and management with industry best practices, ensuring a secure, resilient, and future-ready organization.


