Why Does Your Business Need to Take An AI-Driven IT Security Assessment?
Cyber threats are becoming more sophisticated and pervasive than ever before. The cost of cybercrimes will exceed $10.5 trillion by 2024. Considering the extensive penetration of the digital revolution, businesses must conduct regular and updated IT security assessments to mitigate ever-evolving cyber risks and safeguard their valuable assets.
With more than 20 years of experience, iLink Digital has been providing comprehensive security solutions tailored to meet the dynamic demands of today’s digital businesses. In this blog, we will discuss the risks of neglecting updated IT assessments, introduce you to our AI-driven 4-step assessment approach designed by our Microsoft Certified security experts, and explain how you can leverage your security reports post-assessment to enhance your security plans and strengthen your overall cybersecurity posture.

The Risk of an Outdated IT Security Assessment?
Outdated security risk assessment often acts as a blind spot for businesses, making exploitation more likely to succeed and detection of any vulnerabilities more difficult. This results in compromised security with an increased risk of data breaches, lack of compliance, inadequate system controls, outdated security protocols, and inefficiencies. Other risks that may go unnoticed include:
- Undetected Vulnerabilities: With businesses handling vast amounts of data, monitoring and analysis become challenging, allowing vulnerabilities to slip through the cracks. This enables attackers to gain undetected access to systems, exposing them to potential data breaches that can result in financial losses, reputational damage, loss of customer trust, and intellectual property theft.
- Emerging Threats: Sensitive information continually evolves, creating new threats. Organizations may miss these new threats without an updated security assessment or fail to respond effectively and promptly.
- Proactive Security Management: Conducting updated assessments helps identify where the security team should focus their time and attention. Instead of a reactive approach, which is usually time-consuming, proactive measures can prevent issues from arising in the first place. This allows the security team to manage other activities rather than constantly fixing threats.
iLink Digital’s 4-Step Approach to Cybersecurity Risk Assessment
Our team of security experts designed this 4 step approach to empower businesses across every industry with 360-degree security evaluation, identifying weaknesses, and offering tailored solutions without disrupting ongoing business operations. These steps include:
# Step 1: Discovery – Deep Dive Assets
At iLink Digital, we leverage LLMs and AI/ML algorithms to automate the detection of vulnerabilities across critical assets such as software systems, shadow IT, and cloud deployments. By analyzing extensive IT system data—including network configurations, user logs, and performance metrics—these technologies uncover patterns, anomalies, and potential vulnerabilities. We assign risk codes, scores, and compliance statuses, empowering businesses to safeguard their assets efficiently, streamline operations, and proactively stay ahead of emerging threats.
# Step 2: Advanced Threat Insight
We integrate real-time threat intelligence and advanced AI/ML-driven vulnerability scanning to identify both known and zero-day risks, including those within your supply chain. Our LLMs and Security Co-Pilots swiftly analyze findings, ensuring proactive defense measures against evolving vulnerabilities. Utilizing AI for user behavior analysis, we offer dedicated security analyst hours, monthly reviews, and access to threat intelligence, enhancing awareness of new and existing threats. Our approach includes diverse analytic techniques, complemented by human oversight for trend analysis and proactive threat hunting, alongside web monitoring to provide actionable insights.
# Step 3: Quantified Risk Impact
Advanced risk management techniques such as business impact analysis and Monte Carlo simulations enable organizations to accurately assess risks’ financial and operational impacts. Moving beyond generic risk scores, these methods prioritize risks based on their true potential costs, guiding decisions on prioritizing risks. AI further enhances this process by automating analysis and providing real-time insights, allowing businesses to proactively manage threats and maintain resilient operations across complex supply chains and vendor relationships.
# Step 4: Actionable Remediation
Our Security professionals use insights from these steps to create personalized recommendations for mitigating risks tailored to meet organizations’ specific needs. Working alongside Security Co-Pilots, our experts guide the development and implementation of solutions, leveraging automation to streamline execution. AI further enhances security by automating response and mitigation actions, swiftly isolating compromised systems, and deploying countermeasures to minimize vulnerabilities and mitigate potential impacts of security incidents.
What will you get from the assessment, and how can you leverage it?
- Prioritized List of Vulnerabilities: Your development team will receive a detailed and prioritized list of vulnerabilities. This allows them to focus on the most critical issues first, ensuring that your system’s most significant weaknesses are addressed promptly. By targeting the highest risk areas, your team can prevent potential exploits that could result in costly breaches or downtime, ultimately saving time in reactive fixes and reducing the financial impact of security incidents.
- Executive Summary: This summary is designed for your executive team and provides a high-level overview of the assessment findings. It includes key insights into compliance requirements and highlights areas that could impact business development. This information supports strategic decision-making and helps ensure compliance with industry regulations and standards, such as GDPR, HIPAA, PCI DSS, etc., saving you from hefty fines.
- Actionable Recommendations: Our assessment also provides actionable recommendations tailored for your Information Security team. These recommendations outline urgent measures to strengthen your security posture, mitigating immediate threats and preventing potential breaches.
Case Study: How iLink Digital Identified and Mitigated Over 31,000 Vulnerabilities for an IT Service Customer?
The customer had a large IT infrastructure and was concerned about its cybersecurity posture, wanting to identify and address any potential vulnerabilities. They engaged iLink Digital to conduct a comprehensive IT security assessment, which included the following:
- Vulnerability Scanning: We scanned the customer’s IT infrastructure for known vulnerabilities. A total of 31,097 vulnerabilities were identified.
- Penetration Testing: iLink Digital simulated real-world cyberattacks to identify how well the customer’s defenses could withstand them.
- Security Posture Review: iLink Digital reviewed the customer’s security policies, procedures, and controls to identify any weaknesses.
The assessment identified a total of 31,097 vulnerabilities, of which 23,956 were closed. The reports provided a “Top 10 CVE ID Vs Inventory” list that highlighted high-risk vulnerabilities, helping the customer focus on the most critical issues first.
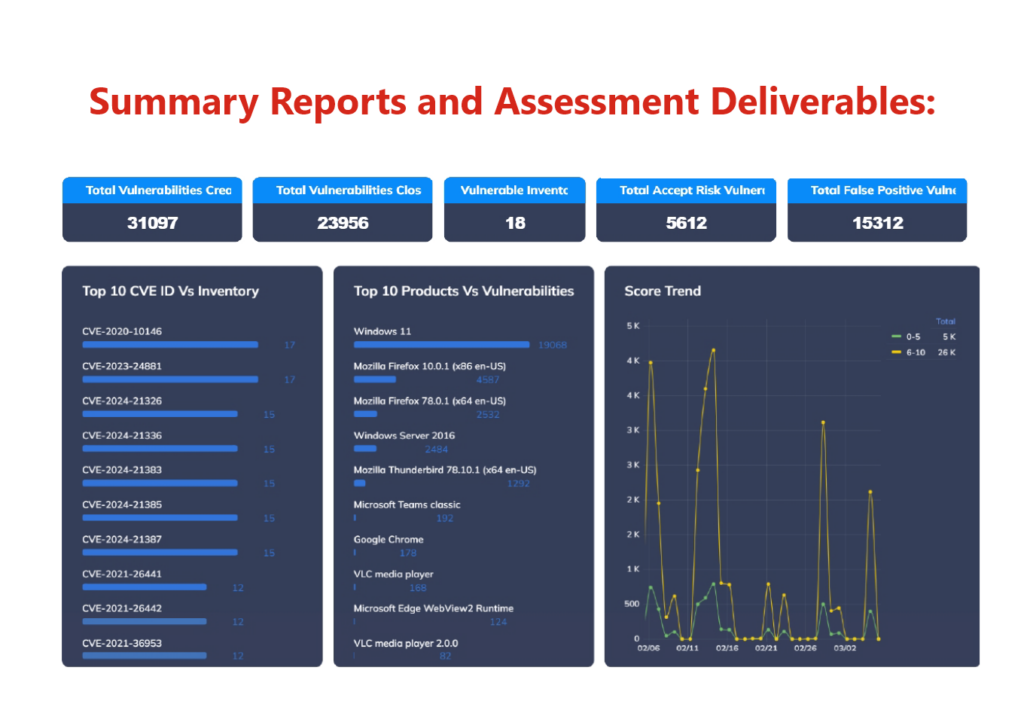
By addressing the vulnerabilities identified in the assessment, the customer improved its overall security posture and reduced the risk of cyberattacks, protecting its reputation, financial stability, and customer data.
However, it is important to note that the specific numbers in the dashboard may vary depending on the customer’s IT infrastructure and the specific security assessment that was conducted.
Conclusion
As cybercriminals constantly employ sophisticated techniques and technologies, business leaders must regularly assess their security controls to ensure defenses are one step ahead. With over 20 years of experience and a team of Microsoft-certified security experts, iLink Digital is your trusted partner in navigating the complexities of cybersecurity.
Contact our security experts today to schedule your AI-driven cybersecurity risk assessment and discover how our tailored solutions can fortify your defenses.



