Why Password-less Authentication is the Future of Cybersecurity?

Introduction
According to Verizon’s Data Breach Investigation Report, “31% of all data breaches over the past 10 years involved the use of stolen credentials”.
As we all know, passwords are the weakest link in the enterprise security infrastructure. Though it has been the primary authentication mechanism for decades, it can be easily stolen or hacked, leaving the user’s network vulnerable to attackers, highlighting the critical need for modern authentication methods. Moreover, remembering and managing complex passwords eventually increases the friction to the user experience. As organizations are finding multiple ways to fortify their defenses, a paradigm shift towards passwordless authentication has emerged as a modern solution, ushering in a new era of security.
This blog delves into how password-less authentication is the next frontier in cybersecurity, exploring its benefits, challenges, and impact on businesses and individuals alike.
Why do we need Passwordless Authentication?
According to Ponemon’s Study, “More than half of respondents prefer passwordless security measure.” Passwords have long been a cornerstone of digital security, yet they are increasingly becoming a liability. People reuse passwords all the time, and unfortunately, they’re so predictable by attackers. Users often have difficulty remembering complex passwords, which leads to weak passwords and the need for frequent password resets. However, the increased reliance on passwords opens the door for vulnerabilities such as phishing attacks, brute force attacks, and credential stuffing.
Challenges of Password-centric Authentication:
- Evolved Enterprise Landscape: As most organizations have adopted cloud-based systems and their remote work policy, the paradigm shift also expands the attack surface, particularly vulnerable passwords.
- End-User Friction: Users are often frustrated with complex password policies due to frequent password changes, leading to an increased likelihood of forgotten passwords and subsequent account lockouts. Moreover, managing and supporting complex password policies require additional IT resources and support.
- Pervasive MFA: Though implementing MFA across enterprise infrastructure will add an extra layer of security during authentication, it often increases user friction and frustration. Moreover, adversaries are evolving with ingenious ways to bypass MFA through phishing, credential stuffing, prompt bombing, and account takeovers, which could result in data breaches.
What Is Passwordless Authentication?
To address these challenges, organizations are increasingly turning to more secure and user-friendly alternatives like passwordless authentication. Fast Identity Online (FIDO) introduced the passwordless authentication standard, FIDO2, which simply takes away the user’s frustration of remembering and storing passwords when setting or resetting passwords, ultimately improving security and providing a better user experience.
It allows users to access their accounts without having to input a password or pre-shared secret. Instead, it provides a more secure and user-friendly authentication method, such as biometrics (fingerprints, face recognition, retina), one-time codes, security keys, and badge-based authentication, to validate a user’s identity. This single-factor authentication is typically harder to spoof and becomes a more reliable indicator of a user’s identity than other factors, helping organizations achieve a higher level of security.
Passwordless authentication offers a promising solution by eliminating reliance on traditional passwords, enhancing security, and streamlining the user authentication experience.
According to Gartner, “By 2025, more than 50 percent of the workforce and more than 20 percent of customer authentication transactions will be passwordless.”
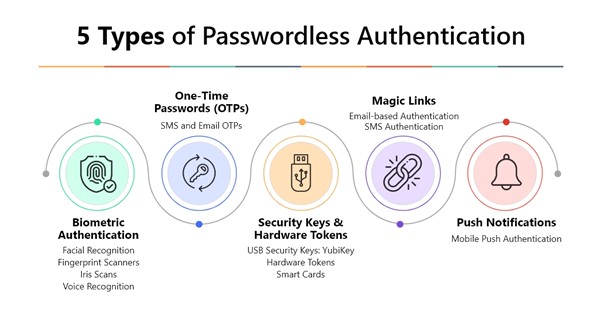
Most Common Passwordless Authentication Methods:
Common methods of passwordless authentication include the following:
- Biometric Authentication: Using unique physical trials such as fingerprints, facial recognition, or retina scans to verify user identity.
- Hardware Tokens: Devices like YubiKeys that generate unique authentication codes.
- Magic Links: One-time links with embedded tokens sent to a user’s email, enabling users to log in without a password.
- One Time Passwords: One-time passcodes delivered via SMS, email, or authentication apps.
- Push Notifications: Authentication requests are sent to a registered mobile device.
FROM PASSWORDS TO PASSKEYS: FIDO2 ALLIANCE
Traditional password-less credentials require users to register on each device and service separately, which can be frustrating and may drive users to insecure fallback options like legacy passwords if a device is lost or stolen. To solve this, FIDO2 introduced passkeys, a secure and seamless way to authenticate across multiple devices. These credentials are stored in the user’s cloud account, ensuring they remain accessible even when switching devices.
If a user has registered their passkey on a mobile phone but needs to log in from another device, they can authenticate using their phone without needing to re-register. This process is designed to be intuitive, secure, and convenient, using Bluetooth Low Energy (BLE) or Near Field Communication (NFC) to verify the presence of both devices nearby.
Benefits of Going Passwordless Authentication
Harnessing the benefits of passwordless authentication lies in its ability to bridge the gap between usability and security. More recently, FIDO2 and WebAuthN provide users with a phishing-resistant authentication capability that leverages common platform-based authenticators to ensure security in a more convenient manner.
- Enhanced Security: Passwordless systems minimize the attack surface for hackers by eliminating weak credentials and reducing susceptibility to phishing and brute-force attacks. Microsoft reported a 50% reduction in compromised accounts after adopting passwordless authentication internally.
- Improved User Experience: Passwordless authentication simplifies login processes by eliminating the need to remember complex passwords that adhere to stringent password policies. This streamlined experience is particularly beneficial in e-commerce, where friction during checkout can lead to cart abandonment.
- Enhanced visibility & Control: These password-less methods are coupled with specific devices or unique user attributes (biometrics), significantly enhancing visibility and control over authentication and reducing the risk of credential theft and unauthorized access.
- Cost Savings: Gartner estimates that 20-50% of IT help desk calls are password-related, costing businesses an average of $70 per call. By implementing password-less authentication, organizations can significantly reduce support costs.
What keeps organizations from Going Passwordless Authentication?
There are several factors hindering enterprises from adopting passwordless authentication, such as existing legacy systems and applications, cost, compatibility issues, usability, and accessibility challenges. Transitioning to a passwordless system may cause disruptions in daily operations, especially in firms with complicated, antiquated systems.
Let’s look at some cons of the passwordless shift that most businesses are experiencing,
- Costly upgrades: Upgrading legacy systems to accommodate passwordless authentication can be costly and time-consuming, necessitating frequent infrastructure modifications.
- System incompatibility: Some older systems do not accept modern authentication techniques, resulting in potential integration difficulties.
- Resource constraints: Upgrading legacy systems may necessitate specific technical knowledge and resources.
- User Acceptance and Training: Organizations ensure a frictionless transition to the new paradigm by providing adequate training to users for the first couple of weeks.
- Regulatory Compliance: Ensure that password-less authentication adheres to relevant regulatory requirements for data protection standards such as GDPR and PCI DSS.
- Risk Management Strategies: Continuous monitoring of the security landscape is critical to promptly addressing emerging vulnerabilities and threats. Regular security assessments and penetration testing can identify weaknesses and help ensure the resilience of the authentication system against evolving threats.
Key Considerations for Organizations to Embrace Password-less Journey
Moving to passwordless authentication is not just a technology change but also a mindset shift for all stakeholders—user, security, business, and technology teams. Organizations evaluating passwordless authentication should consider the following while developing their adoption strategy:
- Assessing Security Requirements: Before implementing passwordless authentication, organizations should conduct a thorough security audit to evaluate authentication flows, data sensitivity, compliance requirements, and current cyber threats. This assessment ensures the right security measures are applied based on user roles and system classifications. Adopting standardized risk assessment frameworks like NIST or ISO helps in systematically identifying threats and aligning security controls.
- Define Programme Goals and Outcomes: Define program goals and outcomes based on the organization’s strategic vision, security, privacy, usability, and regulatory compliance.
- User Experience, Communication, and Training to Maximize Adoption: End user acceptance and adoption of passwordless authentication is critical for successful implementation.
- Start on Low Hanging Fruits: Discover applications with the maximum business impact that are best suited for the end user demographics and technology needs. Learn and build from the initial success to eventually extend adoption to the rest of the enterprise landscape in a phased manner.
Emerging Trends in Passwordless Authentication: Zero Trust in Passwordless Journey
Passwordless authentication is reshaping the digital security landscape, driven by the increased demand for secure solutions in remote and multi-cloud environments. Decentralized identity (DID) models are gaining traction among enterprises, as they can independently manage their digital identities with enhanced privacy and security. Passwordless authentication seamlessly fits into the Zero Trust security framework since it fundamentally follows the least privilege principle, requiring verification at every stage of user interaction across the network.
Conclusion
While deployment costs, regulatory standards, and user readiness may impact full-scale adoption, legacy, and modern authentication will continue to push passwordless authentication to the forefront. Going passwordless is a strategic shift towards enhancing security while providing secure, fast, and frictionless digital experiences that optimize employee productivity, reducing unnecessary password reset-related expenses while protecting your organization against costly data breaches. However, it requires careful planning, effective change management, and a deeper commitment to strike a balance between security and usability throughout the transition.
As organizations embark on their passwordless journey, they need to keep in mind how the user experience, security, and technology readiness are addressed.


